KeePass placeholders are a powerful feature that can save time configuring and maintaining large password databases and add custom behaviour to suit your workflow and preferences.
Since KeePassRPC 1.8, you can use placeholders anywhere that you would normally include a form field value. This includes the standard KeePass username and password fields as well as any custom form field that you configure for an entry.
Warnings
 General use of placeholders
General use of placeholders
It is possible to configure your entry form fields with placeholders which will reveal information that you did not intend to. The scope of what can be revealed is as wide as the entire contents of your password database and even some information about your computer. You can view the documentation on the KeePass website to see what information can be accessed using placeholders.
 Plugin placeholders
Plugin placeholders
Some plugins enable additional placeholders. You should ensure that you understand the security impact of using these plugins and weigh that against any perceived increased convenience. For example, the KeeOTP plugin allows you to store the information required to use your KeePass database as a 2nd factor authentication token.
This essentially guarantees account compromise if your password database is compromised, negating one of the protections of multiple factor authentication. In some targeted social engineering attack scenarios you may not even need to intentionally utilise the corresponding placeholder ({TOTP}) in order to allow an attacker to authenticate as you.
This is a complex topic and one that is not specific to this one example plugin so you should ensure you understand the risks before proceeding.
Limitations
It is not possible to execute local programs. The {CMD... KeePass placeholder is disabled for security reasons.
Enabling the feature
This feature is disabled by default and can be enabled in one of two ways:
For the entire database
This is not recommended because it significantly lowers the barrier for an attacker to access your data (explained in the warnings above).
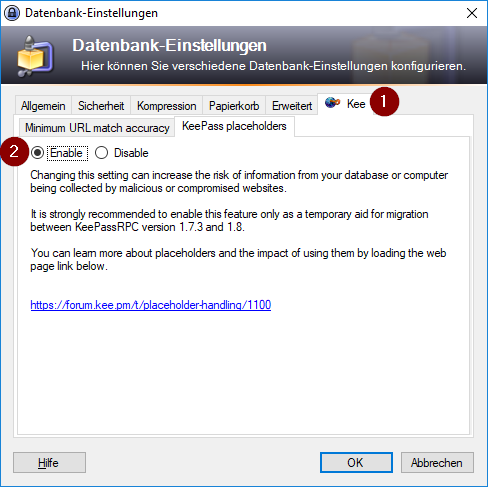
If you do need to enable it (perhaps for test purposes or in already low-security environments) you can do so via KeePass > File > Database settings… > Kee tab > KeePass placeholder tab.
The following screenshot of the Database Settings dialog illustrates this.
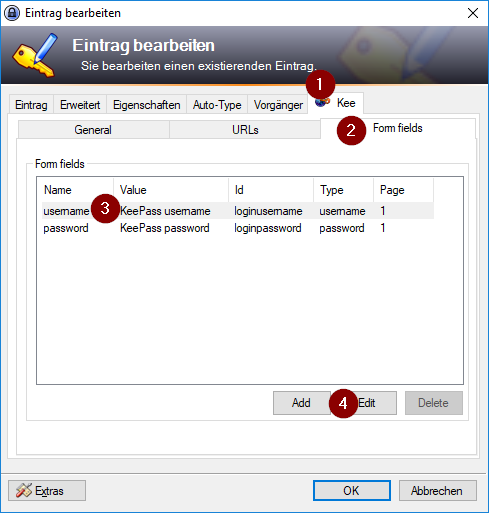
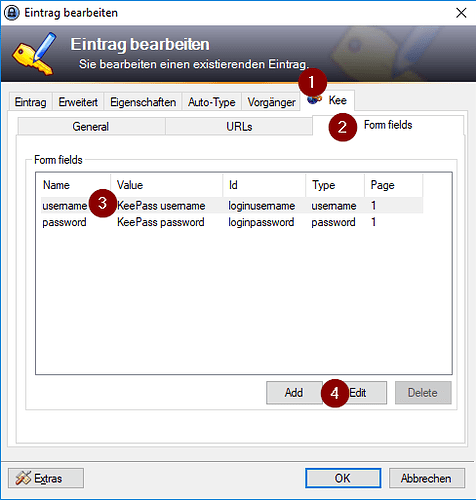
For individual form fields
Open and edit the specific entry in KeePass and then:
- Click on the Kee tab
- Click on the Form fields tab
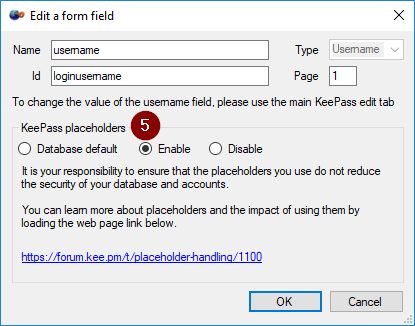
- Select the form field that contains the placeholder (in this example, the main KeePass username field)
- Click on the Edit button
- Click on the Enable radio button
Then click OK until you’re back to the main KeePass window and save the changes to your database.
The following screenshots courtesy of @proxymus illustrate the main steps in the process.
Finding entries that contain placeholders
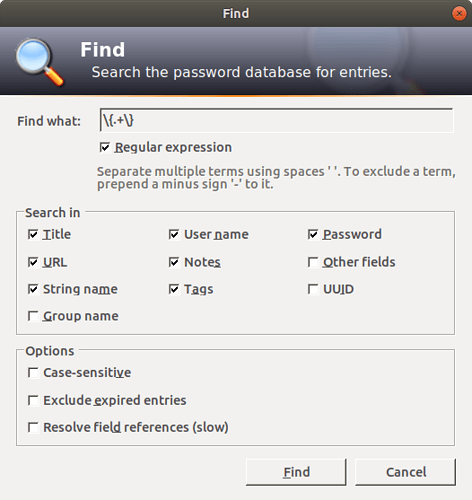
To aid with migration from KeePass 1.7 or earlier, you may want to find all entries that contain placeholders.
We’re not aware of any specific support for this functionality within KeePass but using a regular expression in the find window should get you pretty close:
You could also search “Other fields” but this will find all entries with Kee configuration data (and probably that of other KeePass plugins too) so if you need to do this, you will most likely need to build some far more complex regular expressions to ensure you don’t have an unmanageable number of false positive matches.
Examples
{TOTP}
Setting up 2FA/MFA code auto-completion for a website typically involves a modification to your entry (per the instructions in the comment below) or the creation of a new entry that’s specific to the TOTP form field.
In many cases (e.g. Google, GitHub, etc.) you will also need to add a whitelist entry to Kee so that it knows that you want this field to be treated in a similar way to a username or password field. This essentially overrides the protections that normally prevent Kee from filling usernames and email addresses into search boxes (for example). See: Documentation about whitelisting and some screehshots specific to configuring a whitelist entry for {TOTP}.
TODO: Better examples, screenshots, etc.
 )
)