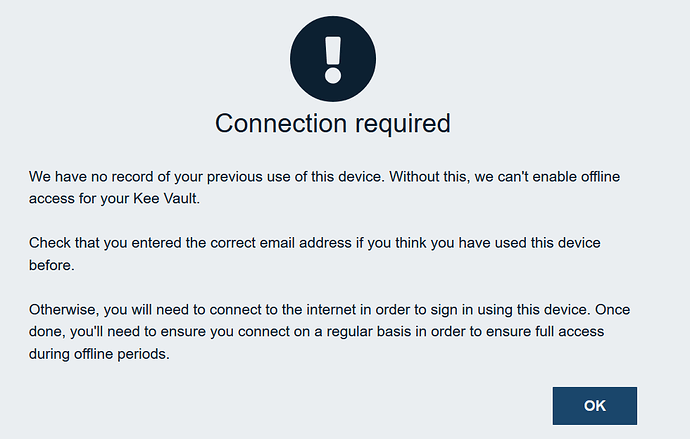
I have been using Kee Vault since its release but offline mode does not function.
Welcome to the forum!
Please can you provide a bit more information about your system to help us work out why it is not remembering your earlier sign-in to Kee Vault.
Have you tried on multiple browsers or devices?
One thing that first comes to mind is that you may have configured your browser to delete all offline content when you close it (or perhaps a browser extension does this for you).
I hope you’re finding Kee Vault useful apart from this issue.
PS: I split your post to a separate topic since this isn’t technically a known issue yet… our investigations may lead us to that conclusion in the end but there is hopefully a simple explanation waiting to be found!
Thanks for the prompt reply. You were correct, I had Firefox deleting content when it closed and that was preventing offline functioning. After correcting, offline functions (not really sure how I would use offline function however).
I really like the new system but I have concerns about data in the cloud. Can you steer me toward info that may address those concerns?
Great! I’m glad that has sorted it. You might be interested to see the future enhancement that we have planned to help make it easier for people to work out what is going on without needing to seek help here.
Yeah I probably should come up with a clearer marketing message about the benefits of Offline support - off the top of my head, it can be useful for things like accessing local devices (phones, Wireless networks, physical safes, alarms, etc.) as well as other apps that are available when offline. It provides protection against Kee Vault service failures too - that’s a more difficult message to market I think but the reality is that even with the service being designed for 100% uptime, something, somewhere, somehow, sometime, will find a way to make Kee Vault be unavailable to you while other online services are still ticking along and asking for your password!
There are so many different aspects to the security of Kee Vault and so many different levels of depth that one can go into from the high level “It’ll all be fine; HTTPS, AES and all that Jazz” down to the individual lines of code implementing the security. Every individual is after an answer to a subtly different question but I am on the lookout for what the most common security questions are, with the intention of writing a one-stop source for answers one day.
Until then, I hope the information below is what you’re looking for.
The Kee Vault data is encrypted in the KeePass (KDBX) storage format, using AES-256 and Argon2. So far, despite over a decade of effort, no-one has found a way to break this protection to get into a KeePass database.
Part of the reason for choosing KDBX (KeePass) as the storage format for Kee Vault is because it is well established and proven to hold up to offline decryption attacks. Since KDBX is designed to be safe to share publicly, Kee Vault is secure even if a synced KDBX file were to be released to the public. Of course, good security is about layers of defences and you can see from other information about Kee Vault and its source code that other layers of defence are also in place to further increase security.
If you really are able to keep your locally stored passwords hidden from the rest of the world forever then you are exceptional (some might also say an optimist). For a lot of people though, what matters more than keeping the encrypted data in a secret location is the security of the data itself, such that if (pessimists may say when) the data is exposed, there is no way to decrypt that data into a form that reveals the secrets (passwords) protected within. As explained above, KDBX has inherent protection against this risk.
The one thing you can never see for any cloud service, even an Open Source one, is what really happens in that service with regards to enabling access to the encrypted data. However, since you can see that only the complete KDBX file is transferred from your device to our cloud, the potential risk in the worst-case is no greater than the risk posed by an offline attack (i.e. the protection from technologies such as Argon2 limit the rate at which an attacker can attempt to break into the encrypted data). As a matter of fact, we don’t provide any mechanism for an attacker to perform mass attempts to guess the password to your encrypted data but even if we were lying or mistaken about this claim, the inherent protection from the KDBX format would kick in at this point, making an attack futile.
Thanks again for the info. Is my vault password ever transmitted and/or stored in the cloud?
No. We don’t even send a cryptographic hash derived from the password so there is nothing for an attacker to target.